Empowering Enterprises to Win More Business!
An enterprise-grade compliance platform + fractional CISOs to keep you compliant and audit ready.

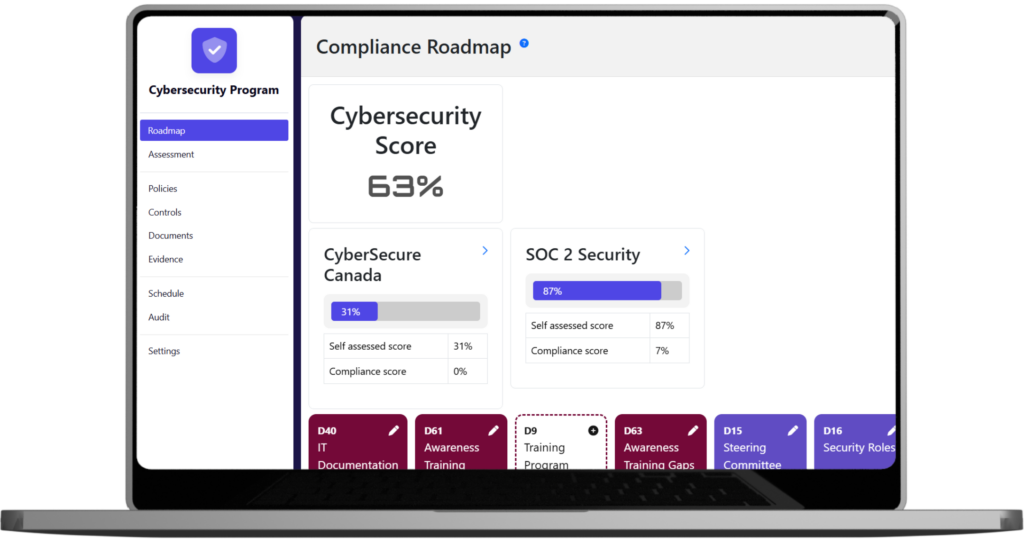
Cocoon CS pairs a powerful GRC platform with fractional CISOs to simplify compliance across 30+ frameworks including SOC 2, ISO 27001, CMMC, GDPR, PCI, HIPAA, and NIS 2.
Automated risk assessments, guided policy workflows, asset tracking, and supplier oversight keep every team audit-ready while turning cybersecurity into a competitive advantage.






